OpenKeychain 3.6: Security Audit and Tons of New Features
Security Audit
We are proud to announce that OpenKeychain has received a security audit where no critical vulnerabilities have been found. This audit has been performed by cure53 and was sponsored by the Open Technology Fund. All identified vulnerabilities have been discussed with cure53 and were properly fixed in OpenKeychain 3.6. We prepared a wiki page including the report and our fixes if you are interested in the gory details.
OpenKeychain 3.6
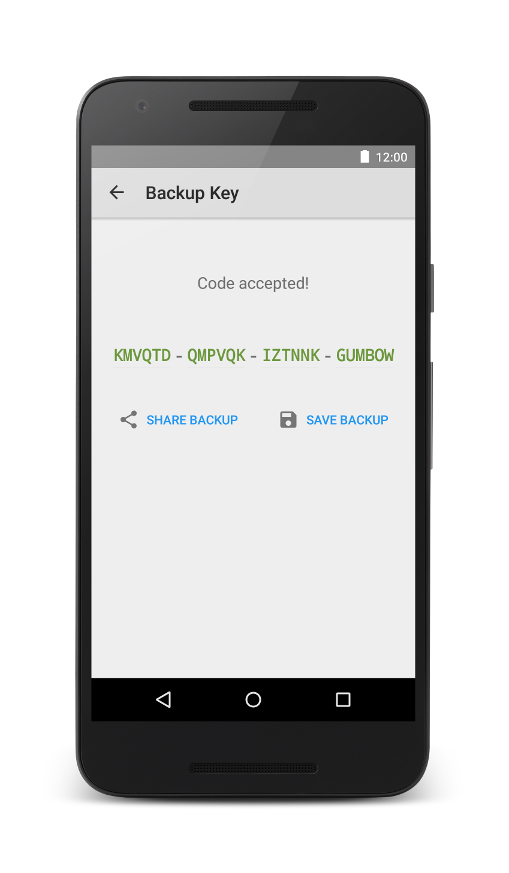
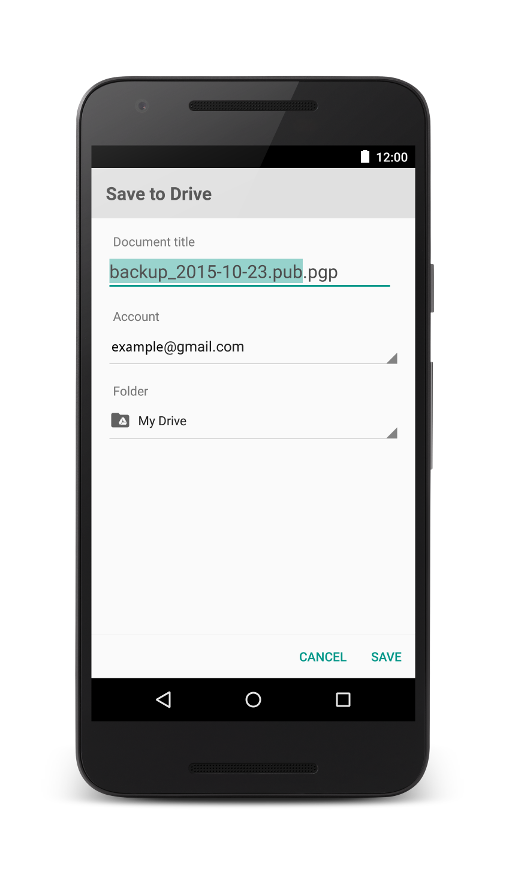
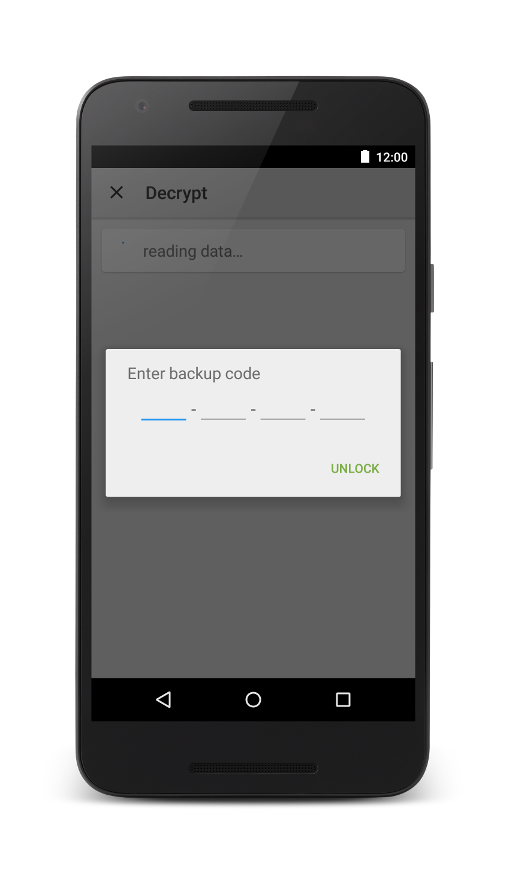
OpenKeychain version 3.6 is an important milestone in our development, not only because of the security audit. Foremost, encrypted backups have been implemented. To keep the list of contacts made with OpenKeychain to yourself, key backups from OpenKeychain are now encrypted by using an automatically generated Backup Code. Write it on a piece of paper and dispose the paper after transferring your keys to your desktop to import them into GnuPG (see our FAQ how to import using gpg). For long term backups, put the paper at a physically secure place. In our opinion, due to the length and randomness of the Backup Codes, you can transfer these backups via cloud storage providers like Google Drive.
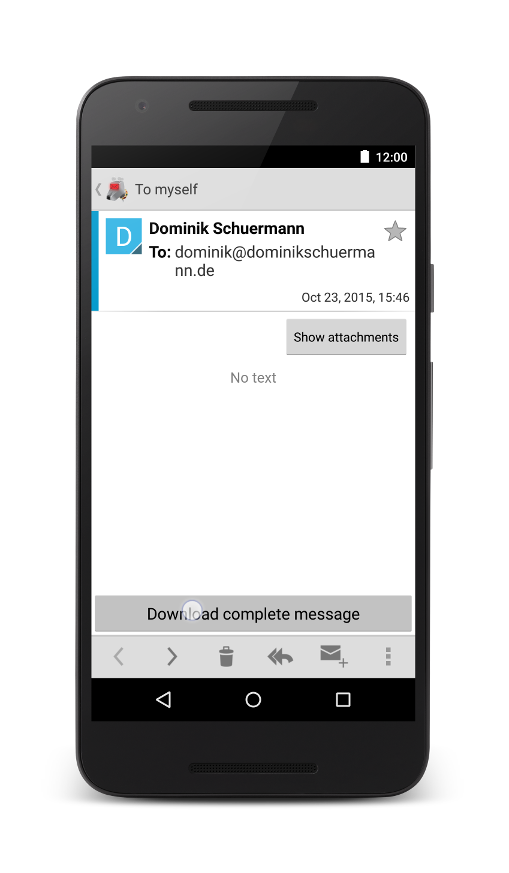
We acknowledge that support for PGP/MIME is currently lacking in most email apps. Until we tackle integrated support for PGP/MIME in K-9 Mail, we integrated a simple MIME parser into OpenKeychain that allows to decrypt PGP/MIME emails. This works from email clients, like K-9 Mail, by downloading the full message, showing the attachment, and then opening the encrypted message with OpenKeychain. Other email clients should be supported in a similar manner. Unfortunately, we still can not provide support for the original AOSP Mail client due to a critical bug in it (not OpenKeychain!).
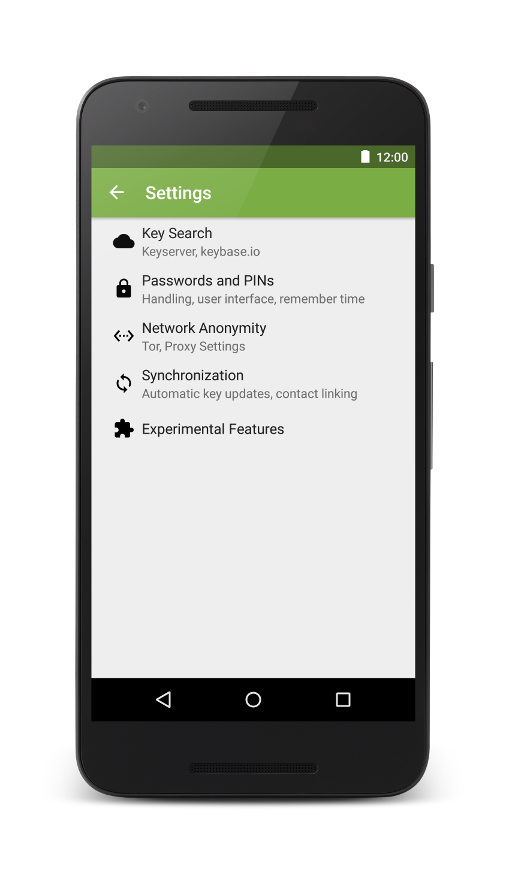
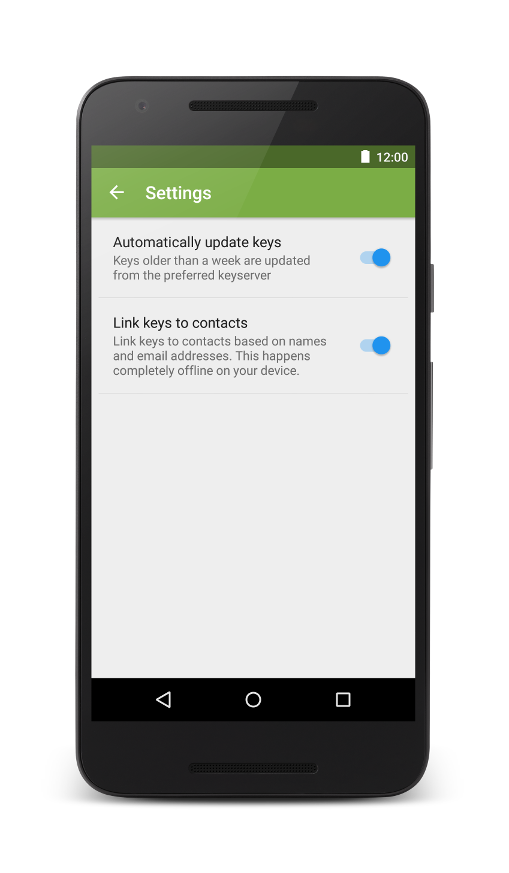
Another cool feature is practically solving the problem that key revocations are often not noticed by users. We implemented automatic updates of OpenKeychain’s key database using Android sync adapters. Every 3 days, all keys that have not been updated for more than 7 days are updated from the pool of keyservers. All updates are executed over TLS with pinned certificates, thus only the keyserver operator could assign these key updates to one IP address. If you are still concerned about your privacy, you can enable Tor support inside OpenKeychain’s settings. While we were at it, we redesigned the settings user interface and introduced a category for experimental features. Besides the most requested feature on Google Play but also most unimportant one for the OpenKeychain developers, the DARK THEME, several features from research conducted at the Institute for Operating Systems and Computer Networks at TU Braunschweig have been integrated. We will likely add more of these settings and feature some of them in our blog.
TLS for openkeychain.org
As a side note: openkeychain.org is now available over TLS exclusively, additionally secured by HSTS.
Changelog of Version 3.6
- Encrypted backups
- Security fixes based on external security audit
- YubiKey NEO key creation wizard
- Basic internal MIME support
- Automatic key synchronization
- Experimental feature: link keys to Github, Twitter accounts
- Experimental feature: key confirmation via phrases
- Experimental feature: dark theme
- API: Version 9
Install OpenKeychain
OpenKeychain is available on Google Play and F-Droid.
- Dominik Schürmann